All hail Keycloak, the protector of realms! 👑🔐
Imagine you’re the ruler of a digital kingdom, and you need to ensure that only the right people can enter your castle, access the treasury, or sit at the royal table. Here’s the great Merlin brings in Keycloak – it’s like Heimdall (the trusted gatekeeper guarding Asgard’s Bifröst) of your realm!
Keycloak is an open-source Identity and Access Management (IAM) solution that acts as the guardian of your applications and services. It’s like having a bouncer who checks IDs before letting anyone in. But Keycloak doesn’t just check IDs; it also manages what people can do once they’re inside, think of it as giving out keys to different parts of your castle based on who’s allowed where.
Here’s a King’s court way to look at it:
- Realm: Your entire kingdom where all your applications live.
- Client: The castles within your realm that need protection.
- User: The citizens of your kingdom who want access to the castles.
- Role: The titles you give to your citizens, like ‘Commander’, ‘Knights’ or ‘Archimage’, that define their access level.
- Scope: The specific gates, party halls, tables or areas within the castle that a role can access, after all mixing peasants and treasury will ultimately lead to a brawl.
With Keycloak, you can let your citizens (users) log in once and move freely between castles (clients) without having to prove their identity each time. This is called Single Sign-On (SSO), and it’s like having a royal decree that opens all scope-based doors for you.
Keycloak also allows users to wear different hats (roles) that give them specific powers (scopes) in each castle (client). And if a citizen/guest from another kingdom (social login) wants to visit, Keycloak can check their credentials too.
So, Keycloak is the gatekeeper, the keymaster, and the royal advisor all in one, making sure that your digital kingdom is secure, functioning orderly, and welcoming those who have the right to enter.
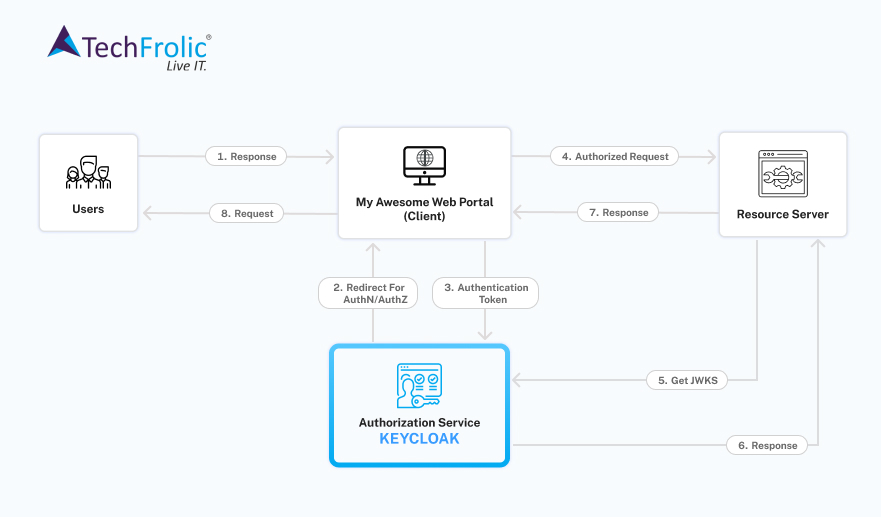
Here’s how Keycloak request flow functions, image courtesy Keycloak documentation.
Keycloak based Identity and Access Management
Fun apart, Security is always a major concern across applications deployed in a distributed or enterprise environment; with the new micro-services architecture, there is no longer a single back-end service, and a need for single Identity and Access provider is felt; Front-end applications invoke multiple back-end services, which may coordinate with other services.
Keycloak is an open-source Identity and Access Management (IAM) solution provided by Red Hat.
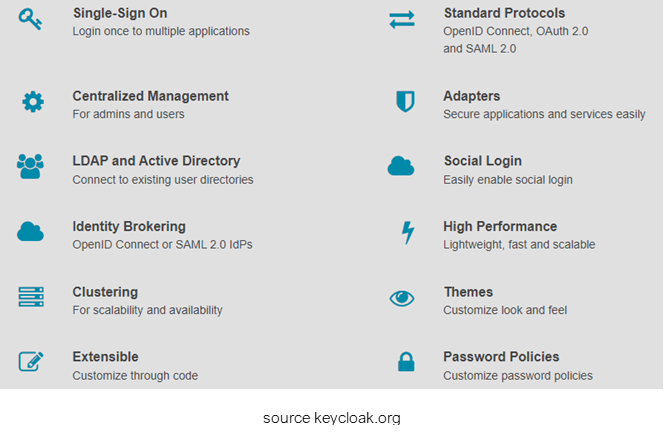
Keycloak offers features such as Single-Sign-On (SSO), identity brokering and social login, user federation, client adapters, an admin, and a user account management console.
In addition to these security features, Keycloak provides customizable themes for web pages and email templates, and its extensible functionalities and domain (custom SPI and REST endpoints).
Keycloak can be used in an embedded mode inside the Spring Boot application.
Spring provides good integration with Keycloak and all the services can leverage a centralised identity provider for authentication and authorization requirements.
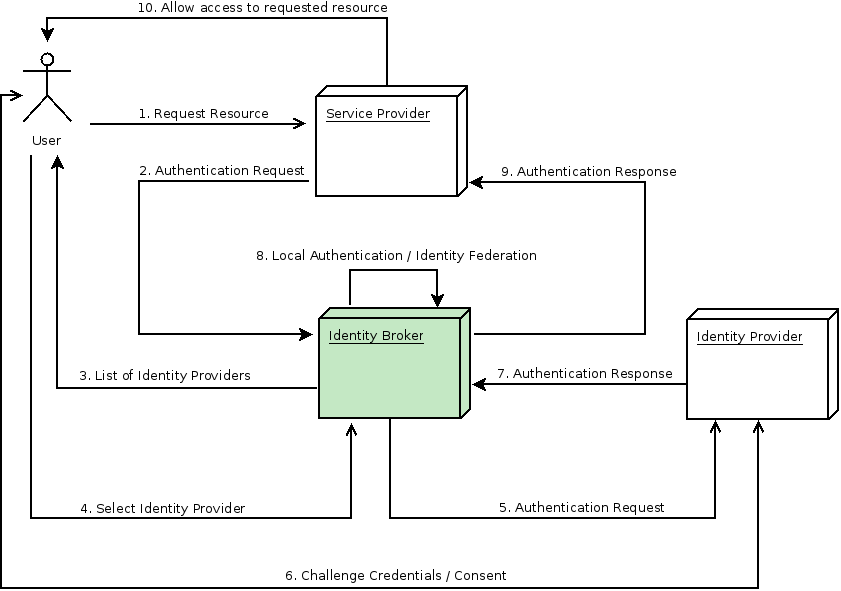
External IAM/IDP workflow with Social login in Keycloak. Image courtsey Keycloak docs.
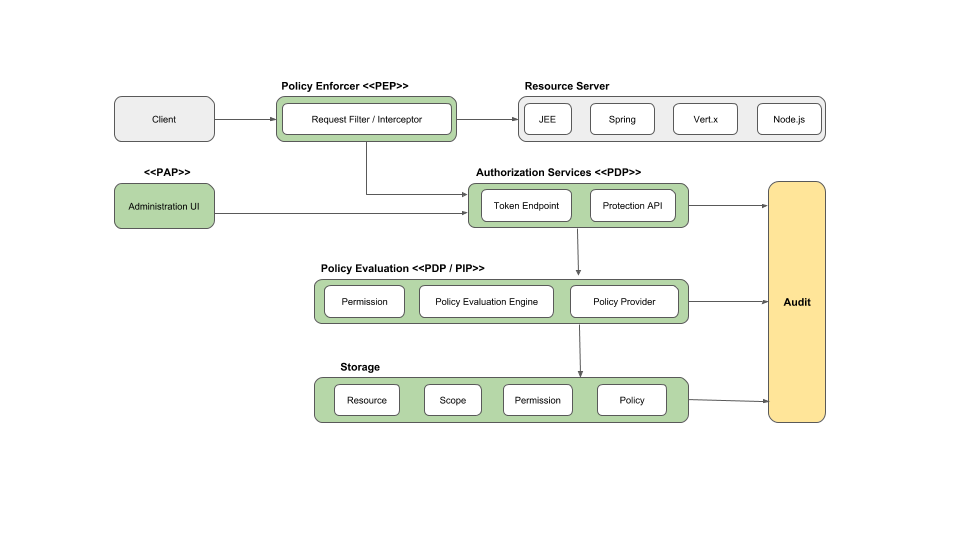
Authorization Policies
Keycloak supports fine-grained authorization policies and can combine different access control mechanisms such as:
- Attribute-based access control (ABAC)
- Role-based access control (RBAC)
- User-based access control (UBAC)
- Context-based access control (CBAC)
- Rule-based access control
- Using JavaScript
- Time-based access control
- Support for custom access control mechanisms (ACMs) through a Policy Provider Service Provider Interface (SPI)
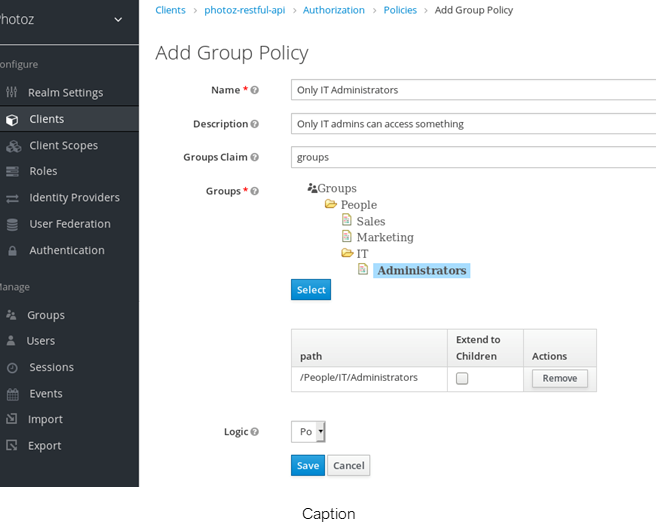
Group-Based Policy
One can use this type of policy to define conditions for permissions where a set of one or more groups (and their hierarchies) is permitted to access an object.
It also has a facility to extend the permissions to all the children of a particular group.
Securing Application and Services
Keycloak supports both OpenID Connect (an extension to OAuth 2.0) and SAML 2.0. you can also choose to secure some with OpenID Connect and others with SAML.
To secure clients and services, you are also going to need an adapter or library for the protocol you’ve selected. Keycloak comes with its own adapters for selected platforms, but it is also possible to use generic OpenID Connect Relying Party and SAML Service Provider libraries.
Keycloak client adapters are libraries that make it very easy to secure applications and services with Keycloak. We call them adapters rather than libraries as they provide a tight integration to the underlying platform and framework. This makes our adapters easy to use and they require less boilerplate code than what is typically required by a library.
Supported Platforms
- Java
- Tomcat
- Jetty 9
- Servlet Filter
- Spring Boot
- Spring Security
- JavaScript (client-side)
- JavaScript
- Node.js (server-side)
- Node.js
- Android
- AppAuth (generic)
- iOS
- AppAuth (generic)
Basic concepts in Keycloak
It has a built-in RDBM system to store login information.
Keycloak operations boils down to three simple terms:
- realm: A realm secures and manages security metadata for a set of users, application, and registered auth clients.
- client: Clients are entities that can request authentication of a user within a realm.
- role: Roles identify a type or category of user. Keycloak often assigns access and permissions to specific roles rather than individual users for a fine-grained access control.
Keycloak offers three types of roles:
- Realm-level roles are in global namespace shared by all clients.
- Client roles have basically a namespace dedicated to a client.
- A composite role is a role that has one or more additional roles associated with it.
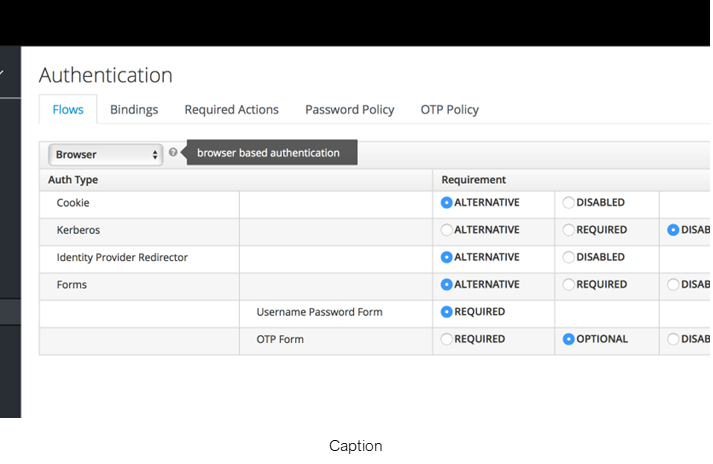
To summarize the key features of Keycloak
- Multiple Protocols Support: Keycloak supports OpenID Connect, OAuth 2.0, and SAML 2.0, providing a variety of authentication and authorization methods for different organizational requirements.
- SSO Capabilities: It offers full support for Single Sign-On (SSO) and Single Sign-Out, streamlining user access across multiple applications, all client apps can easily delegate the request authentication to Keycloak and rest assured that logouts are handled consistently across all the affiliated systems.
- User Identity and Access Management: Keycloak is an standalone user identity and access manager, allowing the creation of a user database with custom roles and groups, can offer permissions based on rules configured in the system.
- RBAC and ABAC: Keycloak supports advanced RBAC and ABAC based authorization.
- Admin Console and API: Keycloak provides both web-based GUI and REST based API for easy configuration and management of Keycloak rules and Users in the associated realm.
- External Identity Source Sync: It can sync with existing user databases, integrating seamlessly with current systems working in an Organization, hence having a minimal impact on existing security apparatus.
- Single-Sign On and Single-Sign Out for browser applications.
- Identity Brokering – Authenticate with external OpenID Connect or SAML Identity Providers.
- User Federation – Sync users from LDAP and Active Directory servers.
- Admin Console for central management of users, roles, role mappings, clients and configuration.
- Account Management console that allows users to centrally manage their account.
- Theme support – Customize all user facing pages to integrate with your applications and branding.
- Two-factor Authentication – Support for TOTP/HOTP via Google Authenticator or FreeOTP.
- Login flows – optional user self-registration, recover password, verify email, require password update, etc.
- Session management – Admins and users themselves can view and manage user sessions.
- Token mappers – Map user attributes, roles, etc. how you want into tokens and statements.
- Not-before revocation policies per realm, application and user.
- CORS support – Client adapters have built-in support for CORS.
- Client adapters for JavaScript applications, JBoss EAP, etc.
- Supports any platform/language that has an OpenID Connect Relying Party library or SAML 2.0 Service Provider library.
Reach out to us for keycloak services….





