Peace of Mind, Anywhere: Relax Knowing Your Network’s Safe with Egress Control
Ensure that you lock and verify things are in order before you venture out.
Do you want to be complicit in a malware or DDoS or phishing attack; or allow your compute resources to be available for illegal crypto mining?
The answer for almost everyone will be a big NO; but unintentionally we sometimes leave the door open for attackers to exploit the vulnerabilities in our system to be used for their sinister motives.
As a network administrator, we mainly concentrate to protect our systems from external attacks while assessing our security perimeter; however, an equally important aspect is to safeguard our systems and not allow an attack phishing or DDoS emanating from our servers.
What is Egress or outward traffic?
Egress traffic refers to network traffic that originates from inside an organization VPC (AWS) (or at least from a node of your network connected to the internet) and is going to an outside destination. It may be desired for fetching information from authoritative sources or integration with external API’s or HTTP servers or software components carrying out routine tasks like updates and patch management. For e.g. consider you have a simple web-based TODO app which also shows today’s weather information from AccuWeather this would require our server to fetch this information from AccWeather servers (like API call or gRPC)
Why should we restrict egress traffic?
Restricting egress traffic has several benefits, some of them are :
- Preventing Data Leaks: Egress filtering controls what traffic is allowed to leave the network, which can prevent leaks of internal data.
- Blocking Malware Communication: If a system is compromised with malware, the malware might try to “call home” to a command-and-control system on the Internet to get additional code downloaded or to accept tasks from a control system. Blocking outbound traffic can help stop this from happening.
- Preventing Misuse of Resources: By blocking certain types of traffic, it prevents your machines from being used for DDoS attacks, malware hosting, spamming, and botnets.
- Regulating Network Traffic: It allows you to regulate what kind of network traffic is permitted to leave your network, giving you more control over your network’s activity.
In most cases the default configuration of firewall or router is to treat and forward any traffic it receives from any source; they can be deceived by IP spoofing thru which an attacker can compromise a host on our network and use IP spoofing to DDoS attack another or to conduct any spam or phishing attack.
The goal of restricting egress traffic is not only about preventing infections, but also limiting the damage and impact if a system has been compromised.
Egress traffic enforcement
There should be a well-conceived and designed organizational policy to protect one’s resources.
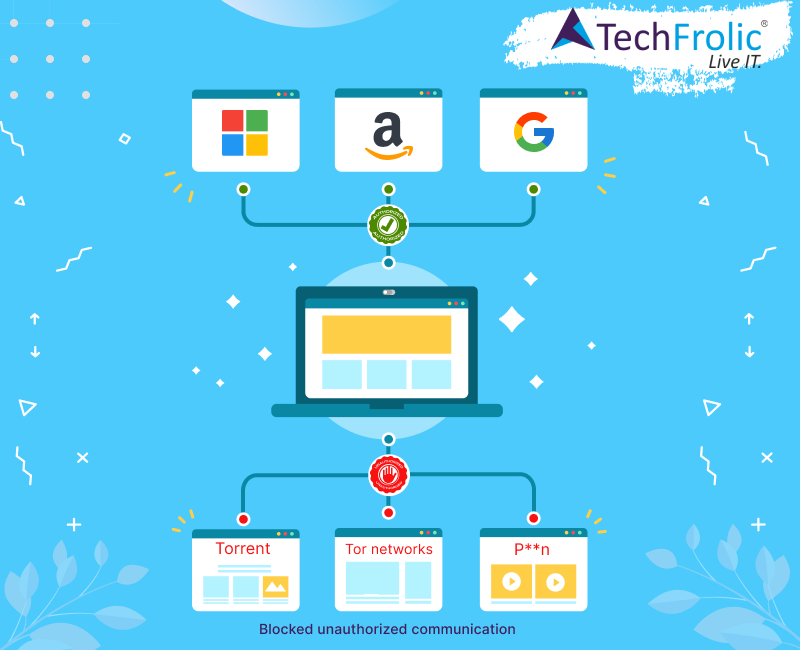
Compose a list of approved (whitelist) internet-accessible services like DNS, POP/IMAP, SMTP, NTP, TCP/IP, HTTP; we should also include a block list (blacklisted destinations) like botnet, adult, games, leisure or in some cases entertainment providers that should be restricted.
There could be cases where certain restrictions may be eased for a group of users, in this case permission sets for User-groups can be applied and by also having a plan of action if a node or network is compromised.
One of the easy ways of restricting is to configure egress traffic filtering policies to deny ALL outbound traffic, it simply means that nothing leaves my network without explicit permission. Next, we can identify the legitimate external access services and granularly apply policy to allow them.
There are several ways to restrict egress traffic, filtering with firewall rules is one of the most basic and effective against this threat.
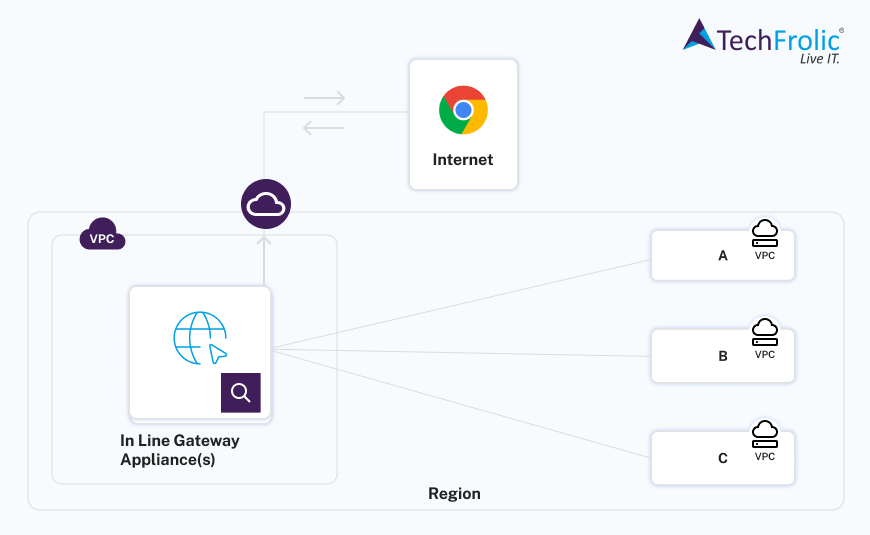
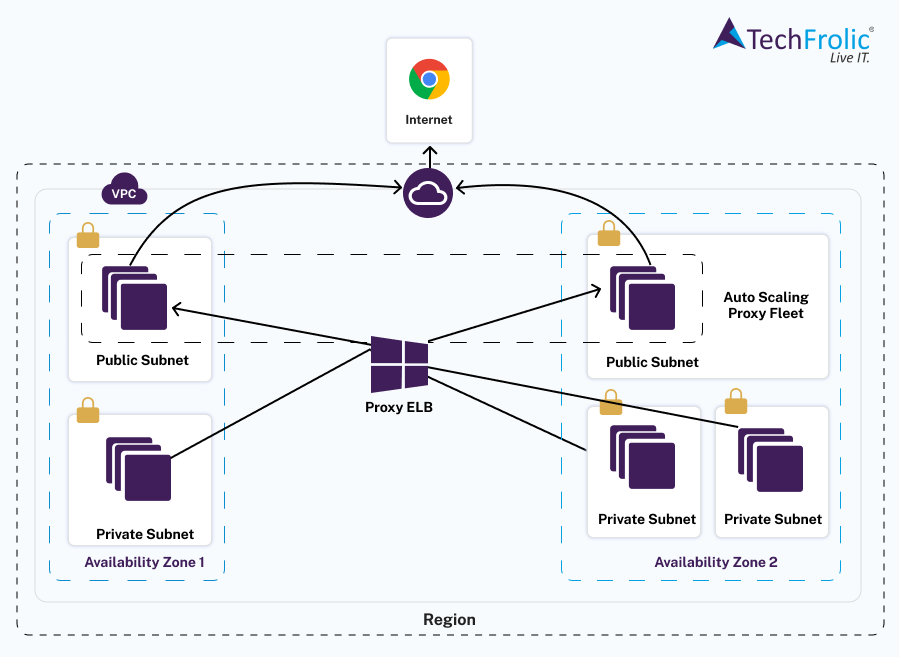
Restrict internet access thru Authorized sources
For firewalls the default egress policy for trusted network is to any source address in outbound packets. If the source address is correct, the firewall will forward it. This is very permissive for any network, and it should be disabled. A configuration of IP subnet numbers or static I/p addresses of hosts that are trusted to make use of hosted services.
Block I/p spoofing: only allow source addresses from the I/P subnet we configure to pass thru our firewall (this may include primary or secondary subnets)
Only allow traffic from addresses we use: Apply appropriate subnet masks to internal networks.
Block traffic from private addresses and VLAN groups: block traffic from connected nodes that should not establish client connections. For e.g. connected nodes in a LAN may rely on internally provided services like DNS, mails and shouldn’t be connected to any other external service.
Block broadcast traffic: Many Network threat service providers maintain lists of networks that are compromised and hijacked by spammers and offer them as public service. This can be used by network admin to filter and apply the traffic rules.
Restrict internet-accessible services
- Only allow outbound connections to those services that your egress traffic allows.
- Only allow client hosts to access authorized services from trusted hosts/servers (whitelisted).
- Manage DNS resolvers responsibly (another topic in itself 😊 )
- Only allow access to ports that the internal servers rely upon to operate correctly.
- Only allow outbound connections thru firewall from proxies.
- If you have internal DNS services, use internal resolvers for forwarding traffic in your internal network, try to have a split DNS. it is recommended to have FQDN (fully qualified domain) for your private name space.
Testing and Monitoring Egress Policies
Run address and port scanning tools to confirm that your white/black labeled results are as expected. Log both allow/deny connections, this will help in later analysis of what is working and if any fine tuning should be made.
NMap, OpenVas, Burp are some OSS that can help in vulnerability scanning and plugging.
Apply notifications to network admins for potentially dangerous outbound addresses, this will help investigate if an infection has already happened and needs to be contained.
Not to mention configuring and maintaining firewall is a special skill and one can easily become an expert in this with practice and practical experience.